Table of Contents
amazon Webroot SecureAnywhere Internet Security Complete reviews
Introduction
Cybersecurity, in this date and age, is paramount. With the increase in instances and levels of sophistication of cyber threats, individuals and organizations find themselves in urgent need of security solutions to secure sensitive data from any unwarranted access while ensuring a safe online working environment. Webroot SecureAnywhere Internet Security Complete (Webroot SIC) is one such solution designed to protect users in a truly all-around way against a barrage of cyber threats. This review covers various aspects of Webroot SIC, including features, performance, user interface, customer support, and general efficacy. Therefore, an examination of these facets will lead us to a coordinated appraisal of the software’s capacities and usability.
Features
Webroot SIC comes with a wide range of features that cover several layers of protection:
Real-Time Threat Protection: This includes real-time protection against viruses, malware, spyware, and ransomware. By being placed in the cloud, Webroot reduces the time to identify and stop new threats or newly emerged threats.
Identity Theft Protection: Webroot itself covers protection features against identity theft of personal information such as usernames, passwords, or credit card details. Webroot always checks for suspicious activity and even warns the user of possible identity theft attempts.
Firewall and Network Protection: The firewall looks at the incoming and outgoing network traffic, thereby preventing unauthorized access to the system and protecting against network-centric attacks. Also included are network protection features, which protect users against phishing attempts and malicious websites.
Password Manager: The Password Manager thus helps users create, store, and manage strong, unique passwords for their online accounts. Password Manager adds security through lower chances of password-related breaches.
Backup And Sync: The App provides for 25GB of online storage meant for the secure backup and synchronization of important files. This feature ensures that a user to be able to restore his or her data in an event of hardware failure, data corruption, or accidental deletion.
System Optimization: Webroot also has a set of optimization tools to boost device performance. These tools are programmed for the removal of temporary files, control of startup items, and for system settings optimization.
Web Protection: This provides browser extension protection against rogue sites, phishing, and online scams. They work cross-browser as protection against all undesirable internet experiences.
Performance
Performance is a very important parameter in security software, as the user will be looking for protection that does not interfere with the speed of use of the system:
Lightweight Design: Webroot SIC is lightweight because this software works over the cloud, so it does not need to have a huge signature database on the user’s device. This requires very little in terms of resource consumption by the system and operation remains unperturbed.
Quick Scans: Engineered for speed and efficiency, the Webroot scanning engine allows its quick scans to be finished in a mere couple of minutes, while complete system scans can be sustained in a rather speedy fashion. Therefore, it is a highlight option of the application to conduct deep scans unabated by the performance of the system.
Real-Time Updates: Webroot uses a cloud architecture, guaranteeing that users will protect themselves against the newest threats in a real-time nature, opening the possibility for constant threat data analytics to provide protection without an updating mechanism for the user.
Minimal Impact on Boot Time: Opposed to most other security solutions, Webroot imposes minimal boot time slowdown, so the users would not have felt the need to complain about slow performance right after opening their devices.
User Interface
The Webroot SIC user interface is designed thoughtfully to ensure that it is intuitive and user-friendly:
Dashboard: The main dashboard presents information about the security status of the system clearly. Users can see whether protection is available on their device or not, view the results of recent scans, and access core functions from one place.
Navigation: The navigation is simple, with tabs and sections quite clearly labeled. Users can access the different features of the software, be it a scan, identity protection, password manager, or backup, very quickly without having to go through extensive menus.
Customizability: For example, users can customize scan areas and shut down their personal firewall settings, adjust the way backups are performed, etc. This adds to the user experience.
Alerts and Notifications about Threats: Webroot notifies users whenever threats or security issues are imminent. Notifications are informative without being obtrusive and don’t bother users with too many pop-ups.
Customer Service
Customer support has become tremendously effective in reaching out to the users for ensuring that they do not have a bad experience while using security software:
Different Support Channels: Webroot provides various support channels, including free phone support, live chat support, and email support; thus, when they need assistance, customers can choose the one that fits their lifestyle.
Knowledge Base: The knowledge base occupies a vast area of the Webroot site, which has articles, FAQs, and other tutorials. It augments the user’s knowledge about the application process, the solution to frequent mistakes, and ways the software minimizes damage by optimizing security settings.
Community Forum: Webroot boasts a lively community forum, where users can post their questions, share experiences, and seek advice from other users and Webroot staff. It’s quite useful when seeking common solutions for well-experienced problems and learning from others’ experiences.
Response Times: This company is known for fast, helpful customer support. Users experience fast response times and provide very effective solutions to problems, which contribute to excellent overall satisfaction.
Overall Effect
It has changed much in the landscape of cybersecurity, and the following is a summary of those changes:
Comprehensive Protection: An all-inclusive suite of sturdy features provides broad protection from the many threats that users may face. Real-time protection, identity theft safeguards, and network security keep users all safe and sound in cyberspace.
User-Friendly Design: Accessibility in design from minimalistic features and operation: features intuitive to the user interface and easy to understand for any kind of experience.-the current outstanding reason why one would choose to go with it is the system performance impact, which is negligible.
Positive Feedback from Consumers: This garnered a lot of positive feedback from consumers towards Webroot SIC-all for these: very effective, very easy to use, reliable customer service. Unique in this product is its selling capacity to achieve great protection without blocking devices.
Innovative Approach: Cybersecurity reaches a new dimension through the cloud-based architecture of Webroot and the real-time threat intelligence. The user receives updated protection without the need to download updates manually because of the capability of the cloud.
Specific Feature Analysis
To appreciate the vastness and breadth of the capabilities of Webroot SIC, it is necessary to analyze each of the core features and functionalities deeply:
1. Real-Time Protection from Threats
Real-time threat protection by Webroot is from a cloud intelligence network that constantly monitors and interprets possible threats:
Machine Learning and AI: Webroot employ advanced machine learning algorithms and artificial intelligence in the identification and eradication or neutralization of threats. With this technology, the software is able to learn patterns and behaviors associated with recognizing malware for the purpose of providing the software with proactive protection.
Behavioral Analysis: Webroot does not depend on signature-based detection alone; it instead relies on behavior analysis in picking out suspicious activities. This helps to identify zero-day threats and polymorphic malware packages traditionally missed by these so-called anti-virus programs.
Threat Research and Intelligence: The software from Webroot keeps updating its database concerning threats that will enable the application to respond quickly to the new threats. A global threat intelligence network compiles this data collected from millions of endpoints to enhance the ability of the software to detect and mitigate risks.
2. Identity Theft Protection
Webroot is a safe harbor for real-time identity theft protection, all-inclusive:
Safe Browsing: This browser extension offers protections against phishing websites and online scams in real time. It blocks websites flagged as harmful, thus stopping people from becoming victims of these schemes.
Password Manager: Protected by LastPass, the integrated password manager is a storehouse of passwords, removing the hassle from generating and using strong, unique passwords per account. Consequently, it reduces the opportunity for theft of credentials.
Credit Monitoring: Webroot includes identity theft protection with credit monitoring to explain any credit change scenarios to a user. Early detection of unauthorized activity may prevent identity theft and ease the effects.
3. Firewall and Protection of the Network
Network security is intrinsic to Webroot SIC:
Outbound and inbound Protection: The inbuilt firewall keeps an eye both on entering and outgoing traffic. Hence this will block a corrupted client in attempting to gain access as well as the outgoing transmission of private data into a malicious server.
Wi-Fi Security: Users’ public network usage is protected by Webroot Wi-Fi coverage. On notifying up unsafe wireless connections, the software protects users from most man-in-the-middle attacks.
Network Anomaly Detection: This feature empowers the webroot network protection with anomaly detection capabilities, which enable automatic identification of unusual behavior within the network. This will detect as well as block any advanced threats that such security measures would have failed to manage.
4. Backup with Sync
The backup and sync functionality of Webroot become so precious with backup and sync because when this helpful feature is not there, major consequences can trigger severe loss of data.
Secure Cloud Storage: 25GB of secure cloud storage has been provided to the user by Webroot so that important files can be backed up. Users even upload and synchronize their files so that the data is accessible always with the most critical ones.
Automatic Backup: This is actually a feature provided by the software that enables users to configure automatic schedules for backing up files. Therefore, it minimizes incomplete manual backups. This reduces the chances of memory loss because of forgetting or overlooking that particular duty.
File Versioning: This feature of the backup brings in the file versioning aspect. Using this feature, the user will be able to retrieve and restore old versions of their files. This feature is essential for many reasons such as undoing the recent changes made and in cases when the file becomes corrupt.
Encryption: Encryption makes sure that all the files saved in the cloud are protected in such a way that unauthorized access cannot take place to an individual’s sensitive information while storing and transferring over the network.
5. System Optimization
Ideal performance of the system at a particular point in time is perhaps one of the finest prerequisite tools when it comes to computing. This is just one of those tools that Webroot has added for the benefit of users, allowing them to.
Junk File Removal: Some junk-file removal functions included with Webroot optimizations solve the problem of the accumulation of temporary files, caches, and meaningless data that can bog down disk space as well as slow a system. Consequently, the performance of any device can be enhanced significantly by performing regular cleanup.
Startup Management: Here is the management of startup items by the program. The users may disable it or postpone the launching of the unwanted program during the time of startup; thus, reducing the boot time and making the system faster ready.
Performance Monitoring: Webroot’s monitoring performance is real, with insights into how much system resources are used. Identify the bottlenecks on performance and allow users to ensure their devices run as efficiently as possible.
6. Web Protection
Webroot SecureAnywhere Internet Security Complete is focused on ensuring safe browsing in protecting its users from the threats in the web:
Phishing Protection: The browser extensions provided with Webroot scan and block phishing sites, thus preventing the users from unwittingly releasing personal information into the wrong hands. This feature is vital to protect sensitive information related by making it difficult to obtain.
Safe Search: Webroot safe search functionality shows users gave security ratings for search sites in search engine results. Thus, it would help the users choose wisely the sites they visit without exposing them to harmful content.
Real-Time Filtering of URLs: This software performs the filtering of website traffic on a real-time basis by blocking access to known malicious URLs. This further enhances the defense against drive-by downloads and other attacks based on the web.
User Experience
The user interface for Webroot SecureAnywhere Internet Security Complete was designed for ease and smoothness:
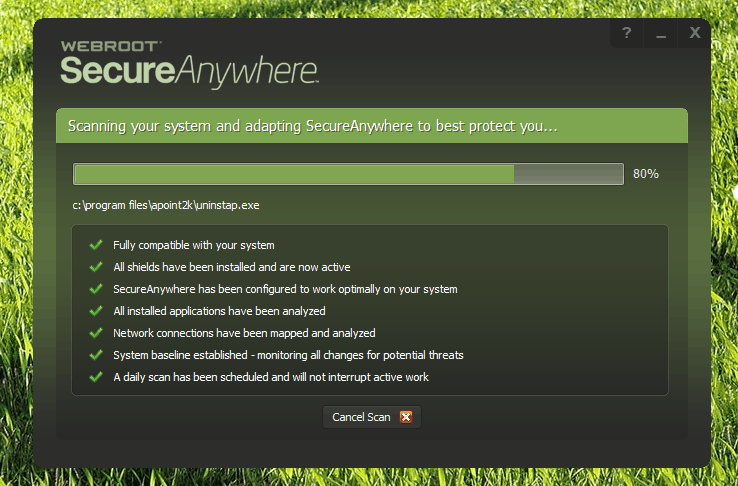
Installation and Setup: Installing Webroot is quick and easy. The installer for the software is lightweight, and requires very minimal input from the user. After installation, Webroot automatically launches for an initial scan of the system for establishing a baseline of security.
Ease of Use: All features are easily accessible, with a clean interface and uncluttered appearance. The main dashboard gives a clear overview of the status of the system, recent scan results, and current security status.
Customization and Control: Default settings are usually fine for general use, but the program’s settings can easily be customized for those who seek more control. Scans, firewall rules, backup scheduling, and other settings may be altered to meet the user’s specific needs.
Resource Efficiency: Probably one of Webroot’s most loveable features is its minimum resource footprint. It allows users to execute scans or concurrent tasks without much system interruption, fitting even for older systems or those that are not so powerful.
Customer Support
Good customer support is one of the primary product offerings of Webroot:
24/7 Availability: Webroot support is available 24/7 using different channels; thus users will always be able to reach an assistant whenever they need. This is especially critical for emergencies that need immediate attention to security.
Expert Assistance: The Webroot support team is generally regarded as being competent and highly professional. Expect knowledgeable and helpful responses to your questions by phone, chat, and email.
Comprehensive Resources: The Webroot support page has an extensive set of resources, with a knowledge base, user guides, video tutorials, and troubleshooting articles. This helps users solve some common problems on their own as well as make the most of the software.
Engaging with Community: The active Webroot community forum allows users to mingle with their peers and the Webroot representatives. This experience is of value in sharing tips, talking about security trends, and asking for help on specific issues.
Effectiveness of Security
The test measure of any security application would actually be how well it protects from threats:
Independent Testing: Webroot SecureAnywhere Internet Security Complete has consistently achieved high marks in independent tests of security conducted by companies like AV-TEST and AV-Comparatives. Those tests analyze the software in terms of its ability to detect and counter a range of malware and other threats.
Real-World Performance: In practice, real-time Webroot protection has been highly successful in blocking phishing and ransomware attacks as well as zero-day threats. Its behavior analysis capabilities identify and actually tries to block these threats before they are able to go around signature detection methods.
Low False Positive Rate: Webroot keeps a very low false positive rate to ensure that very few of the legitimate applications or files get flagged as threats. These issues are critical to maintaining user trust and disrupting their experiences as little as possible.
Impactful and Legacy
Webroot SecureAnywhere Internet Security Complete has made a major difference in the cyber security market:
Innovative Thinking: Merging cloud intelligence and machine learning into a product was a really futuristic approach to security by Webroot. This essentially enables the product to have very high-end protection while remaining very small.
Market Position: Over the years, Webroot has developed into a strong and dependable security provider. Its solutions are adopted by millions of individuals and businesses all over the world, therefore reflecting its tight position in the market.
User Trust: The words of acclaim that have spoken from both users and experts reinforce the image that Webroot has built as a trusted vendor. Its steady performance and very easy-to-use configuration translate into very high satisfaction figures.
Future Proofing: Webroot continually updates its threat intelligence and enhances it through cloud-centric technologies to keep users protected from the dynamically changing cyber world. These advancements keep Webroot ahead for the future.
Conclusion
Webroot SecureAnywhere Internet Security Complete is a comprehensive and effective security solution for users against an extensive range of cyber threats. Real-time detection of threats, identity theft safeguards, and system optimization tools generate powerful defense against modern-day electronic calamities. With a lightweight approach that barely impacts system performance, it becomes increasingly appealing to users who desire secured efficiency.
All through the broad experience, the intuitive user interface, generous customization options, and reliable customer support add to the sauce. Cloud-based tech adoption by Webroot along with real-time threat intelligence guarantees that users remain secured with updates in real time, minimizing manual updates.
Thus, Webroot SecureAnywhere Internet Security Complete could in many cases be viewed as a versatile and user-friendly security suite, offering complete protection without compromising system performance. Because of that effortless operation, including its effective installation and proactive approach to cybersecurity, Webroot SecureAnywhere Internet Security Complete is considered an essential solution for both individuals and businesses in securing their digital domains and protecting sensitive information.
where can i you get a Webroot SecureAnywhere Internet Security Complete online
Webroot SecureAnywhere Internet Security Complete 2013 – 5 Devices: Buy it now
Webroot SecureAnywhere Internet Security Plus 2013 – 3 Devices: Buy it now
Webroot SecureAnywhere Complete 10 Device Family ESD [Download]: Buy it now
WEBROOT SECUREANYWHERE COMPLETE 1PC (WIN XPVISTAWIN 7): Buy it now
Webroot SecureAnywhere Complete 2012 3PC [Download]: Buy it now
Function:
– Protect your computer from these threats.
• Prevents viruses, trojans, spyware, rootkits, and other threats.
• Scan the entire computer within two minutes.
• Prevent the program yet to be identified based on the “expression” suspicious.
• Automatically update the new version.
• Prevents malicious websites before you connect.
• Prevents malicious software when changing the security settings.
• Were include management functions, monitor network connections and firewall.
– Security features uniform mechanism.
• Prevent hackers and online fraud.
• Encrypt and securely store usernames, passwords, credit card numbers.
• Automatically login to websites reliable and secure.
• Create and remember passwords against hackers
– Protect your personal files.
• Improved online data backup up to 30 GB (10 GB per user).
• Synchronize the files, passwords across computers and mobile devices.
• Making the deleted files can not be restored.
– Protect your Android device.
• Scan all threats and automatically fixes.
• Alerts you when your device and settings are attacked.
• Lock or delete data in smartphones, computer remotely.
• Locate your phone or tablet if lost.
– Protect your iOS device
• Update and browser protection for iPod, iPhone, or iPad.
• Ensure the safety of online transactions, financial information for shopping and banking.
• Automatically sync with Webroot’s advanced URL.
System requirements:
• Processor: Intel Pentium / Celeron or AMD K6 Athlon / Duron.
• RAM: 128 MB (minimum).
• Hard drive space: 10 MB.
• Internet Explorer 7.0 or higher, Mozilla Firefox 3.6 or higher (32-bit).
• Internet connection.