Table of Contents
amazon Webroot Internet Security Complete reviews
Webroot SecureAnywhere Internet Security Complete is a professional application provides users with a robust security regime based on the cloud to prevent online threats. Besides, it also owns fast scan speeds and consumes less system resources when compared with other similar product. Thus, do not affect the speed of your computer or cause disruption to the user during use.
Furthermore, by applying analytical tools threats that you can quickly check the file, URL and website simultaneously. The result, prevent threats and new available. Therefore, keep you safe while performing tasks online surfing.
Introduction
Today, cyber security has become a great concern for every individual and organization in the era of digitization. Keeping in view all these aspects, robust security software is the prime requirement to secure sensitive data and online activities. One such product is the Webroot Internet Security Complete, which is a comprehensive package consisting of numerous security features for screening the users against all possible threats. This review will concern different aspects of this special security software, such as features, performance, user interface, customer support, and impact. In this way, we will be able to assess the effectiveness and usability of the software.
Features
Webroot Internet Security Complete offers multifarious protection layers and is packed with features:
Real-Time Threat Protections- Webroot gives real-time protection against all types of threats ranging from viruses, malware, spyware, and even ransomware. Its cloud-based approach allows real-time identification and mitigation of new and emerging threat.
Identity Theft Protection: The software also comprises identity theft protection features, enabling the safeguarding of personal details, for example, usernames and passwords, and credit card information. Webroot watches out for any irregular activity and alerts users in the event of identity theft.
Firewall and Network Protection: The firewall screens the network traffic, which allows a person to keep a check on his or her incoming and outgoing links against unauthorized infiltration attacks. Block Network Protection: Guard against phishing attempts and malicious websites.
Password Manager- The password manager gives Webroot users the ability to create, store, and manage strong, unique passwords for their online accounts. Strong, unique passwords reduce the chance of an occurrence related to breaches of passwords.
Backup and Sync: It has 25GB of secure online storage to back up important files and to synchronize them. This ensures that users will have an option for recovery from hardware failure, corruption, as well as accidental loss.
System Optimization- It consists of efficiency-improving applications that help in the optimization of systems for the users. It cleans temporary files, manages startup items, and optimizes system settings for overall speed and efficiency.
Web Protection: The software is included with browser extensions that will protect users against infected websites, phishing, and online scams. These extensions work with all major browsers for safe browsing experience.
Performance is an important factor in security software because users want protection that does not interfere with the speed of their systems or usability.
Lightweight Design: Webroot Internet Security Complete is well known for being extremely lightweight. It is designed to be cloud-based, thus eliminating the need for much of a signature database present on the users’ devices for this reason, the resource consumption is extremely minimal with smooth performance.
Quick Scans: The scanning engine of Webroot is built for being efficient and fast. The complete system scans are also speedy. The quick scans normally take a few minutes to complete. The ability of the software to perform thorough scans with very little impact on the system performance is really an advantage.
Real-Time Updates: Because of the cloud-based nature of Webroot, it can guarantee real-time updates so that the users are always been safe with the new threats. In addition, the software constantly analyzes threat data all across the world for modern protection, as it does not need manual signing after each update.
Minimal Impact on Booting: These effects do not slow down the start of the system by the other security solutions; this does so by having minimal effects on boot time. Users will receive fast and responsive performance from the instant when they start their devices.
User Interface
It has always been about making the UI of Webroot Internet Security Complete friendly and intuitive for all the users:
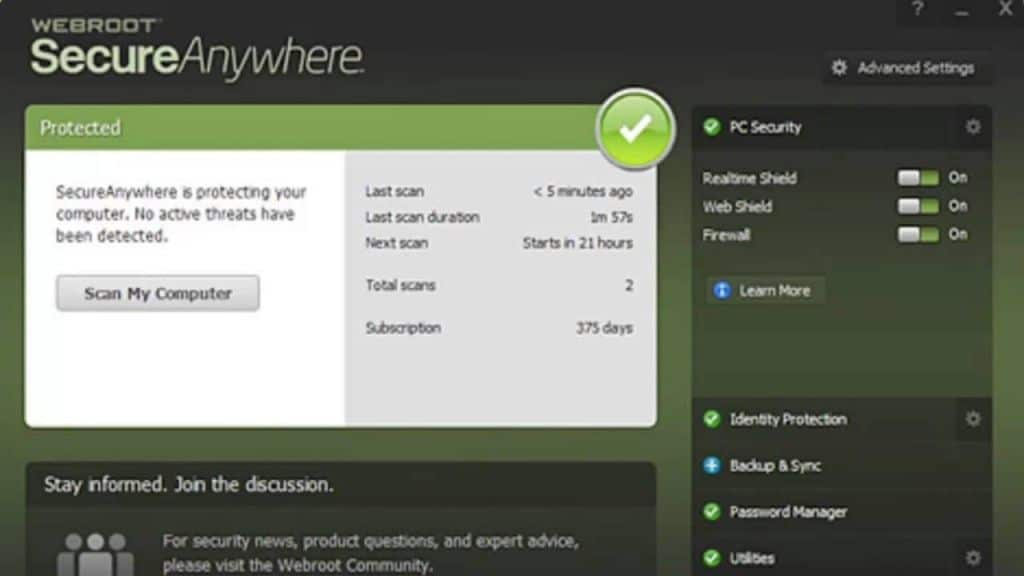
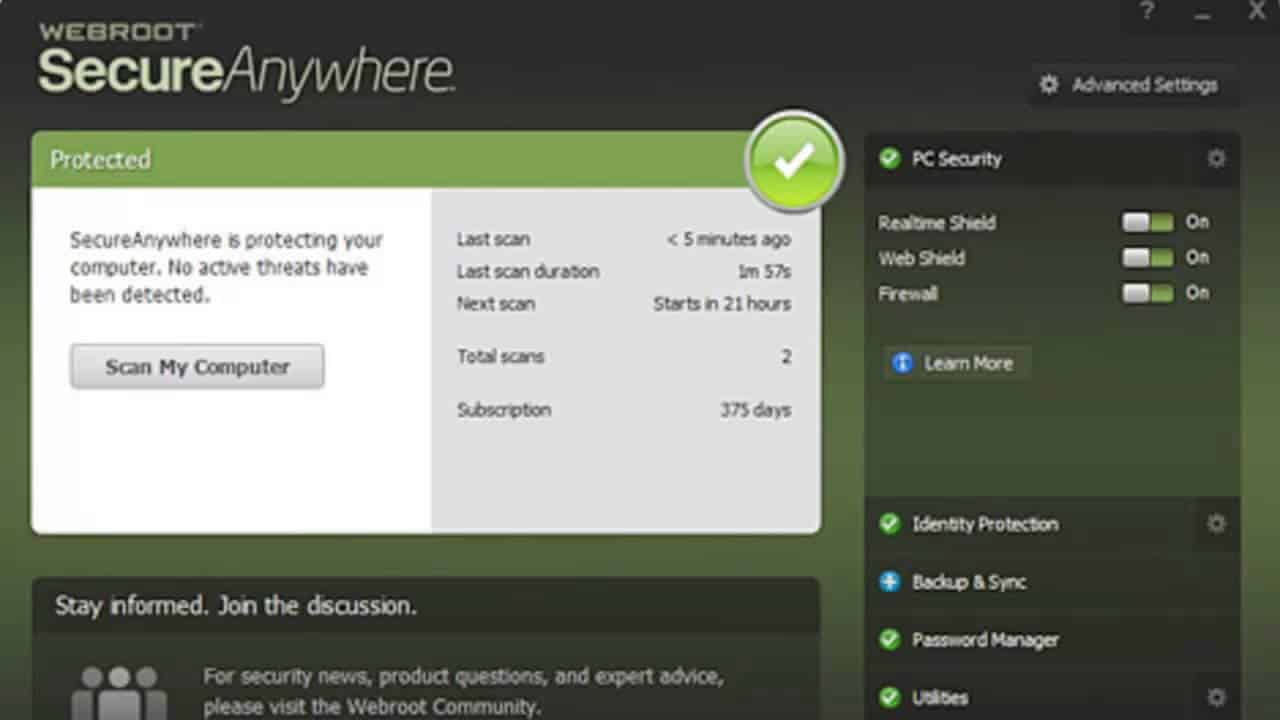
Dashboard: There is a dashboard overall showing a clear overview of the security status of the system. The device protection today viewed recent scans and other relevant features can be accessed from one conve…
Navigation: The entire navigation of the software is simple with tabs and sections clearly labeled. From there, readers go quickly to scan, identity protection, password manager, backup, and all the other features without going through any difficult navigation.
Customization: Webroot offers a lot of options available to cutomize this software according to users’ need, for instance, schedule scans, firewall configuration, and easy backup management. Ability to customize settings gives better user experiences.
Alerts and Notifications: Alerts and notifications related to possible threats and security breaches are delivered by Webroot to the users. Yet the notification is informative but not annoying, giving the user information without a bunch of pop-ups.
Customer Support
Effective customer support is required to address user concerns and improve the experience with security software as follows:
Support Channels: Webroot offers many different support channels onto which its customers can contact the company for purposes of seeking assistance; such avenues here include phone and live chat, or email support through which users would reach out for help in whatever manner the users prefer.
Knowledge Base: The Webroot website includes a rich knowledge base in terms of articles, FAQs, and tutorials. It gives the users much-needed information on employing the software, effectively trouble-shooting some important issues, and maximally securing it.
Community Forum: Webroot additionally maintains an active community forum where users are permitted to ask certain questions, share experiences, and seek advice from other users as well as Webroot personnel. In addition, a good resource for common problem solutions and learning from some experiences of others is available at this forum.
Response Time: Well recognized for rapidity and helpfulness to customers, Webroot offers quick responses and effective resolution of user problems, in total adding up to a positive experience.
Overall Impact
Webroot Internet Security Complete has made a major impact in the world of cybersecurity:
Comprehensive Protection: The broad scope of applications within the whole suite offers good and cohesive protection against many forms of intrusion, including real-time protection against identity theft, while the net security covers the user well across the digital world.
User-Friendly Design: Well-designed user interface and features easy to navigate, so Webroot is, indeed, very accessible to just about anyone in terms of experience. It doesn’t slow anything down.
Positive User Feedback: Users report praising the Webroot Internet Security Complete software for its ability to provide coverage without being obtrusive, making it easy to use and reliable in customer support.
Innovative Technology: In reality, the cloud-based infrastructure as well as the real-time threat intelligence itself is Webroot’s innovative approach on cybersecurity; one can consolidate all the power of cloud use with up-to-date protection for users that is more frequently released without going through manual updating.
Conclusion
Webroot Internet Security Complete’s main plus point is that it is a very powerful yet easy-to-use security solution that protects against many threats. An asset for any individual or a business trying to secure their digital world, its real-time threat protection, identity theft protection, and optimization give it very high marks. A bonus is that it is lightweight and resource-friendly, meaning that users can protect themselves while working on their system at optimum speed.
Although its interface is quite easy to use, other experiences include customization and great customer support. Webroot, therefore, presents an intelligent solution that is founded on an innovative approach toward cybersecurity with cloud-based support and real-time threat intelligence; this means that it is certainly at the forefront of the fast-changing computer security environment.
where can you get a Webroot Internet Security Complete online
Webroot Internet Security Complete 2016 | 5 Devices | 1 Year | PC [Download]: Buy it now
Webroot Internet Security Complete 2016 | 5 Devices | 2 Years | PC: Buy it now
Minimum system requirements:
The chip Processor: Intel Pentium or AMD
RAM memory capacity: 128 MB
Hard drive space available: 10 MB
Microsoft Internet Explorer 7.0 or higher
Mozilla Firefox 3.6 or higher (32-bit only)
Google Chrome 10.0 or more
Internet connection
Some key features:
Protection against online threats have been known recently and unknown, including viruses, spyware, cybercriminals, the threats on social networking, phishing attacks , identity theft, websites / links / results not safe.
Always protect your data and your identity while browsing, shopping, banking or online document sharing.
Providing continuous protection mode without interrupting or slowing down the computer’s startup.
Protect yourself against fake Web sites that try to steal your personal information.
Warn you about infected sites before visiting them.
Protection and simplify the process of managing passwords, so only need to remember one master password and unique.
Automatically back up photos and files with online storage for free 25 GB, so you can access from all your devices.
Provides protection regime social networks, including Facebook and Twitter.
Analysis devices and operating systems to detect problems in the system.
Clean up traces related to online activities and ensure not leave any chance to recover any files that have been deleted.
Automatically scans your Android device and download the app for timely detection of threats.
Lock or delete data in smart phones and tablet PCs from remote locations and help you locate the device is lost or stolen.